HCL Domino V11 – Directory Synchronzation – Part 3
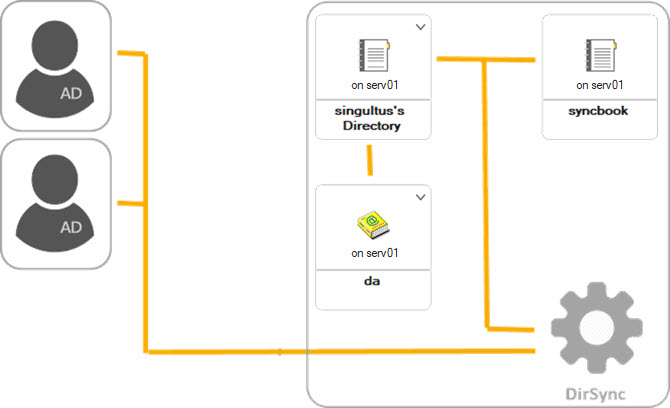
After you have created a Directory Assistance document in part 2 of this tutorial, that is enabled for Directory Sync, create a Directory Sync Configuration document in the Domino® directory. You use this document to select Directory Sync configuration options and then to enable Directory Sync.
Open your Domino Directory (names.nsf) and navigate to Configuration > Directory > Directory Sync .
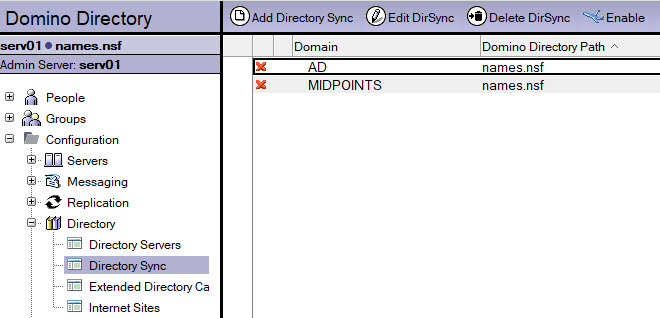
Click “Add Directory Sync” to create a new document.
Select a Directory Assistance Domain from the list of configurations in da.nsf.
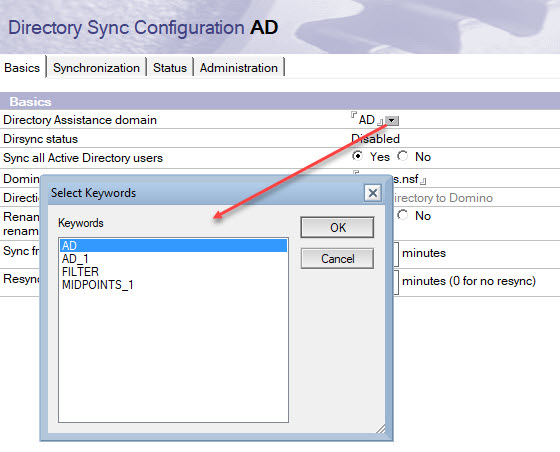
For an initial sync of all users and/or groups from the selected Active Directory set “Sync all Active Directory users” to Yes.
Select No (default) to sync only Active Directory users who are registered in Domino. If previously set to Yes, any unregistered Active Directory users
synced previously are removed from the Domino directory.
For an Active Directory record to sync with Domino, the Active Directory mail field must match theInternet address field in the Domino directory Person document.
Type in the name of the application that is the target for synchronized users and/or groups into the “Domino Directory file name” field. Typically, this is your primary address book (names.nsf)
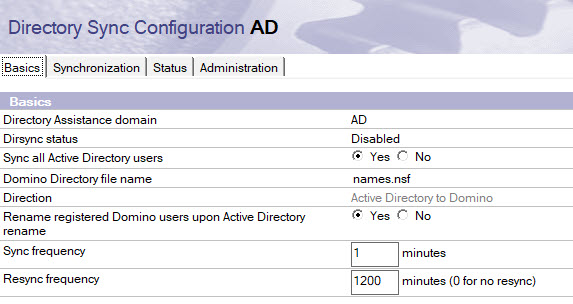
As you can see, the “Direction” field is not editable by now. At the moment, only a sync from Active Directory is possible.
One of DirSync’s abilities is to rename synced users in the target Domino directory when the when the users’ common name changes in Active Directory.
If the name of an Active Directory user who is not registered in Domino® changes, the name is automatically updated in the Domino® directory Person document during sync, regardless of this option.
If the user is already registered, a standard administration process Rename Person request is initiated for each name processed.
The Sync frequency settings tells DirSync how frequently the Dirsync task checks for Active Directory changes to synchronize. Default is once a minute.
Resync frequency tells DirSync how often to resync all data from Active Directory, in minutes. Default is 10,000 minutes or approximately once a week. If you don’t want to regularly resync all data, specify 0 ( not recommended).
If you want to synchronize groups, select the types of groups to synchronize. If you don’t want to synchronize groups, do not select either option on the “Synchronization” tab of the DirSync configuration document.

Keep in mind that the groups to be synced must be in the global group scope. If you try to sync local groups, you will receive an error on the Domino server console.
DirSync DirSync CSyncFromAD::DoModify - Skipping modification because entry = 'CN=Users,CN=Builtin,DC=ad,DC=fritz,DC=box' is not a valid candidate for a 'group' record.
If you only want to sync a subset of all objects under the configured BaseDN, use an LDAp filter.

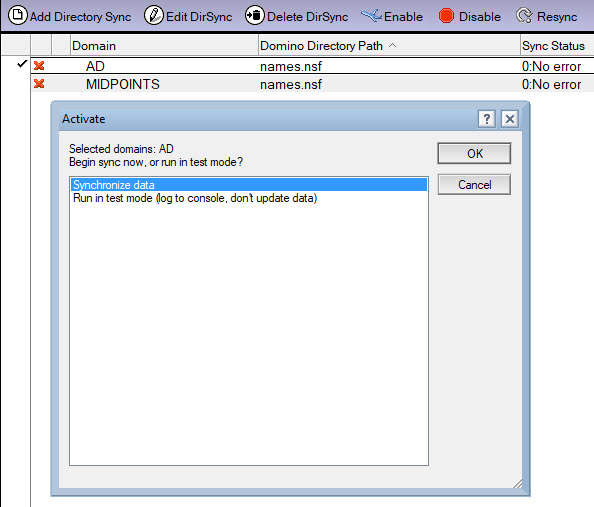
After you finished your configuration, save and close the document.
Select the saved configuration in the view, click Enable and select Sychronize Data. Select Run in test mode to simulate the actions that Directory Sync would take but without changing any Domino® data.
If not already done, add the DirSync task to the server’s notes.ini
ServerTasks=Replica,Router,Update,AMgr,Adminp,Sched,CalConn,RnRMgr,Dirsync
and issue the following command on the server console: load DirSync.
DirSync will be started automatically on next server restart.
The Dirsync task begins to run when it detects the configuration document and you should now see an entry similar to this on the server console.
[1BE0:0004-1D10] 19.01.2020 15:34:09 DIRSYNC From Active Directory (AD) - Summary (0.128 sec, Start=210711, Adds=0, Modifies=0, Deletes=0, Skips=0, Errors=0, End=234710)
Look at the Status tab of the Directory Sync Configuration document in the Domino® directory in addition to monitoring the output of Dirsync at the server console and in log.nsf.
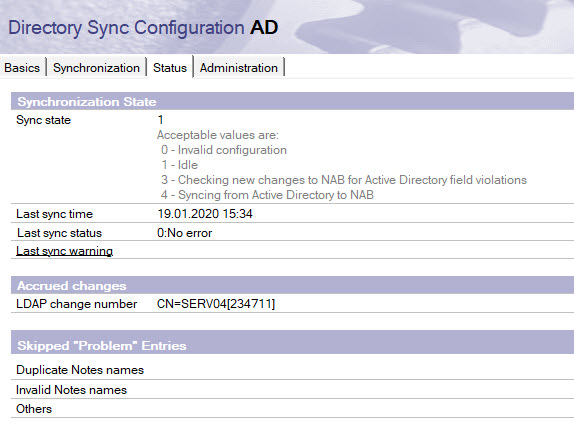
Congratulation, you have successfully configured DirSync synchronization.
In the next part we will dig deeper into DirSync features and abilities.